mirror of
https://github.com/status-im/consul.git
synced 2025-02-22 10:28:31 +00:00
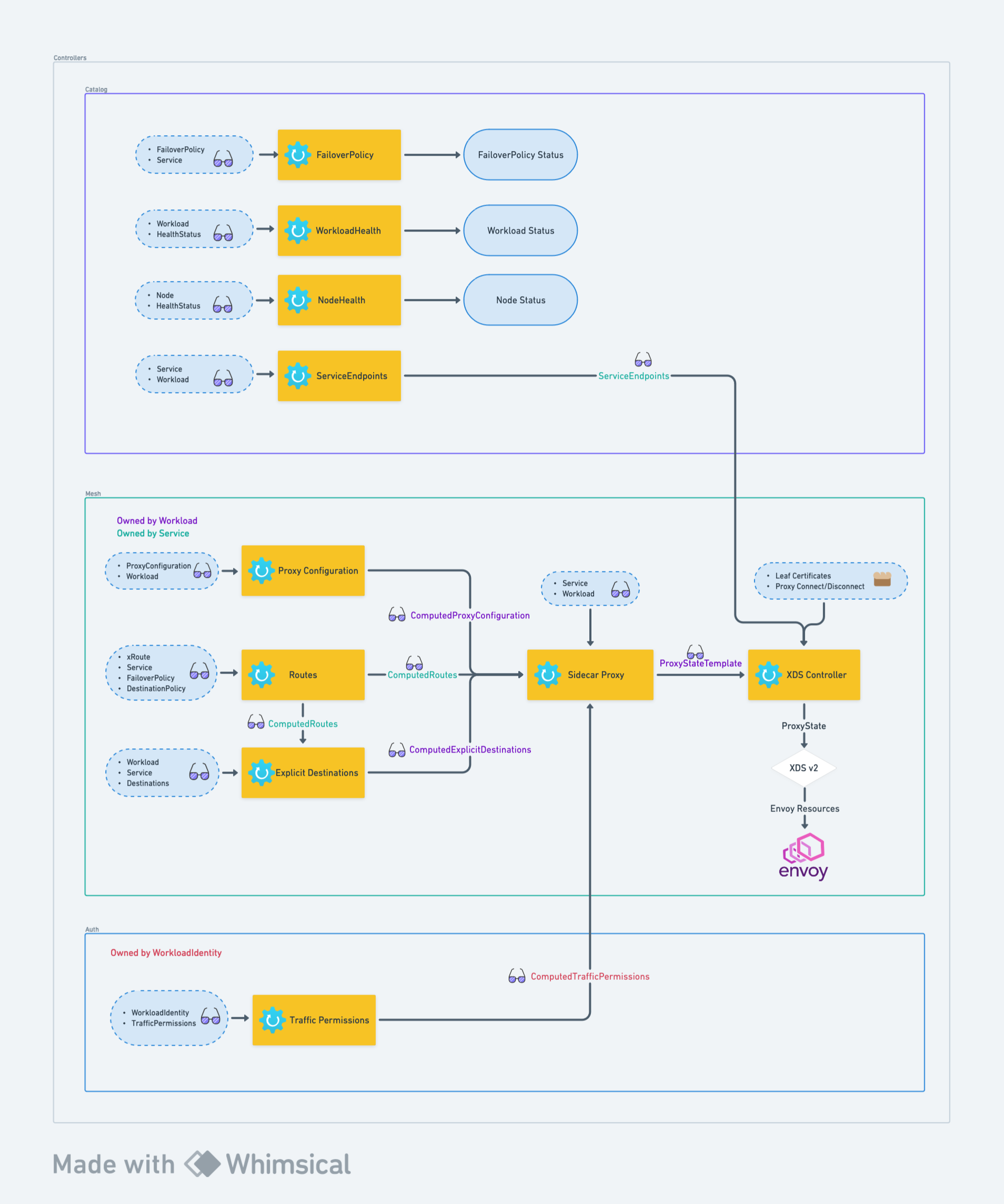
V2 Service Mesh Architecture
In Consul 1.16 and 1.17 releases, Consul's service mesh has been rewritten to use the controller architecture and the resource APIs.
At a high level, the service mesh consists of resources and controllers living in three groups: catalog, mesh,
and auth.
The controllers in each groups are responsible for producing an output that may then be used by other controllers.
-> Note: This diagram is valid as of Consul 1.17. It may change in the future releases.
Catalog controllers
Catalog controllers are responsible for reconciling resources in the catalog API group.
- FailoverPolicy controller validates
FailoverPolicyresource has valid service references and updating the status theFailoverPolicyresource with the result. - WorkloadHealth controller takes in workloads and any relevant health statuses and updates the status of a workload with the combined health status.
- NodeHealth controller takes in nodes and any relevant health statuses and updates the status of a node with the combined health status.
- ServiceEndpoints controller generates a
ServiceEndpointsobject that is name-aligned with a service and contains workload addresses and ports that constitute a service.
Mesh Controllers
- ProxyConfiguration controller generates a
ComputedProxyConfigurationresource that is name-aligned with a workload.ComputedProxyConfigurationcontains all mergedProxyConfigurationresources that apply to a specific workload. - Routes controller generates a
ComputedRoutesresource that is name-aligned with a service. It contains merged configuration from all xRoutes objects as well asFailoverPolicyandDestinationPolicy. - ExplicitDestinations controller generates a
ComputedExplicitDestinationsresource that is name-aligned with a workload. It contains mergedDestinationsresources that apply to a specific workload. - SidecarProxy controller takes in the results of the previous three controllers as well as some user-provided
resources and generates
ProxyStateTemplateresource which serves as the representation of Envoy configuration for sidecar proxies. - XDSController takes in
ProxyStateTemplateresources, fills in missing endpoints references as well as certificates and CA roots and sends them over to another component that sends this information over to Envoy.
Auth Controllers
- TrafficPermissions controller generates
ComputedTrafficPermissionsresource that is name-aligned withWorkloadIdentity. This computed resource contains all traffic permissions that apply to a specific workload identity.